🔍 Securing the User Journey Without Compromise
At Apollo, we believe that security and user experience should never be at odds. As our platform scaled and threats grew more persistent, we set out to evolve our defenses in a way that preserved performance, respected user flow, and hardened our backend against sophisticated, high-frequency abuse. This journey led us to a modern solution for basic attacks: Cloudflare® Turnstile.
This blog shares how we transformed reactive, manual security workarounds into a smart, adaptive challenge system—driven by data, integrated across surfaces, and built for real-world threats.
🚨 Real Threats, Real Stakes
Towards the end of last year, we experienced a sharp rise in credential-stuffing attacks and bot-driven API abuse. Our login and signup endpoints, along with several high-traffic APIs, were heavily targeted. Notably, the login endpoint saw a significant spike in 4xx responses—revealing a large volume of failed authentication attempts.
Upon deeper investigation, we identified these as suspicious and coordinated attempts resembling a DOS-style credential stuffing attack, aimed at overwhelming our authentication infrastructure.
While we didn’t experience any outages — and our systems aren’t that brittle — these types of attacks, in general, can strain backend systems and potentially lead to degraded user experiences. This might include slower response times, increased login failures, or occasional lockouts. In extreme cases, they can even cause false positives or erode user trust if security mechanisms respond too aggressively.
While we had already invested in robust infrastructure-level defenses, the growing sophistication of these attacks made it clear: we needed a smarter, more adaptive solution—one that could deliver enhanced protection without compromising on a seamless user experience.
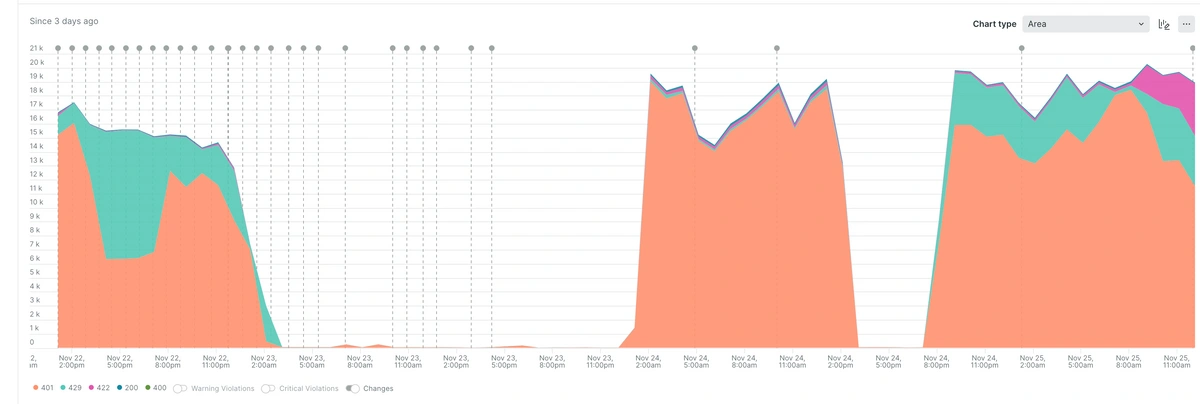
The chart above illustrates a surge in failed authentication and login attempts over a three-day window, as visualized through a breakdown of HTTP status codes. Notably, there’s a recurring spike in 401, 429, and 422 responses.
🛡️ Introducing Cloudflare® Turnstile: Modern Security, Human-First
Fortunately, by the time these attacks escalated, we had already completed the design and early implementation of Cloudflare® Turnstile—a privacy-centric, next-gen CAPTCHA alternative purpose-built to distinguish real users from bots with zero friction to legitimate users. Our first version was deployed in tandem with Cloudflare® WAF, aligning with their recommended pattern for secure fetch-request validation at the edge.
Turnstile stood out for three key reasons:
- It delivers a seamless, background validation experience—comparable to modern invisible CAPTCHA solutions—while avoiding reliance on intrusive heuristics or behavioral profiling.
- It offers privacy by design, avoiding cookie-based tracking and aligning with GDPR and global data protection standards.
- It offloads token validation to the firewall edge, significantly reducing server-side overhead and simplifying backend logic.
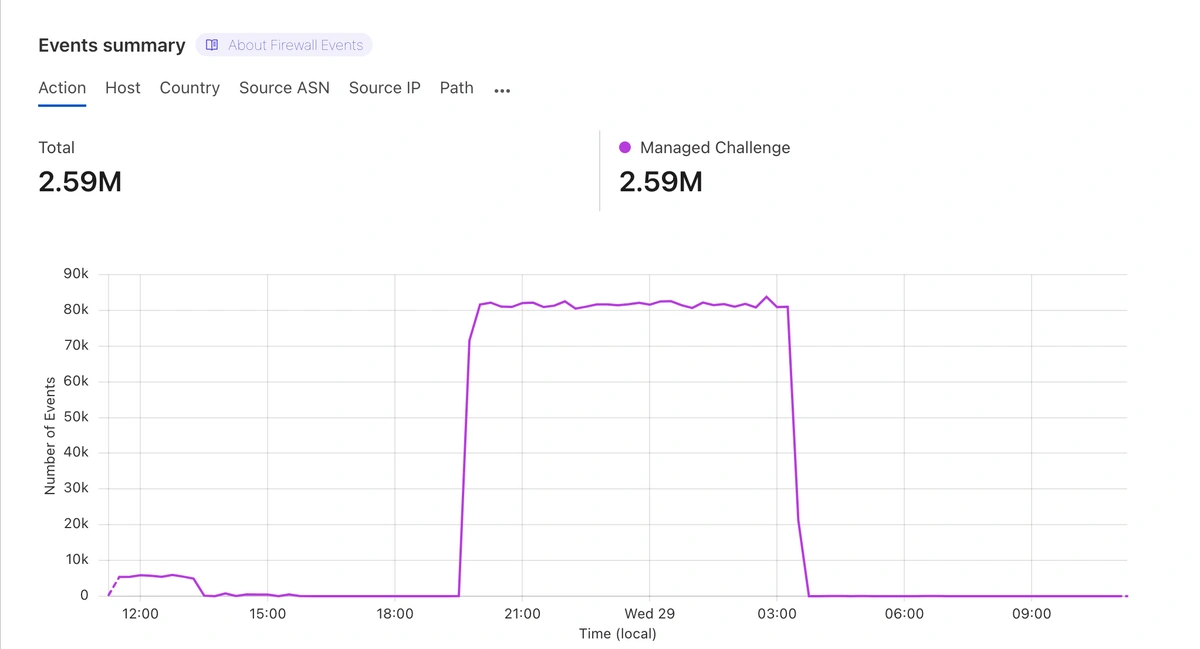
This strategic investment enabled us to respond quickly—with a solution that elevated both security posture and user experience. Notably, it helped us successfully mitigate one of the largest bot attacks we’ve seen to date—over 2.6 million requests with a 0% solve rate, providing broad and immediate protection across our stack.
Over a span of several hours, more than 2.59 million managed challenges were triggered, with a sustained spike of ~80,000 events per minute during peak activity. Remarkably, the solve rate was 0%, confirming that the defense mechanisms were effective in identifying and blocking all malicious automation
✳️ Where We Integrated It
- Login & Signup Flows (main web app + marketing site)
- Mitigation efforts are focused on high-abuse APIs — especially the critical prospecting and enrichment endpoints within the web app
- Chrome Extension to maintain consistent security across surfaces
But at Apollo, we didn’t just drop in a widget—we designed a context-aware, deeply integrated challenge pipeline.
🚀 How We Engineered Precision Defense
1. From Manual Rules to Adaptive, User-Aware Challenges
A Web Application Firewall (WAF) is a security system that filters, monitors, and blocks HTTP traffic to and from a web application. It works by applying predefined rules to detect and prevent common attacks like SQL injection, cross-site scripting (XSS), and bot abuse.
While WAFs are effective at blocking known threats, they can sometimes be too aggressive, flagging legitimate users as malicious. That’s why we built a more adaptive, user-aware approach that uses contextual signals to make smarter decisions.
-
Backend Intelligence
-
Our Ruby service dynamically decides when to trigger a challenge based on user or team context, request path, rate limits, and anomaly patterns observed on the web app.
For example, if a free-tier user is aggressively hitting the “add to prospect” API, we may surface a challenge to validate the legitimacy of the activity. Once the challenge is completed, the user can continue seamlessly. This helps us distinguish real users from headless browsers or bots.
-
-
Frontend Experience
-
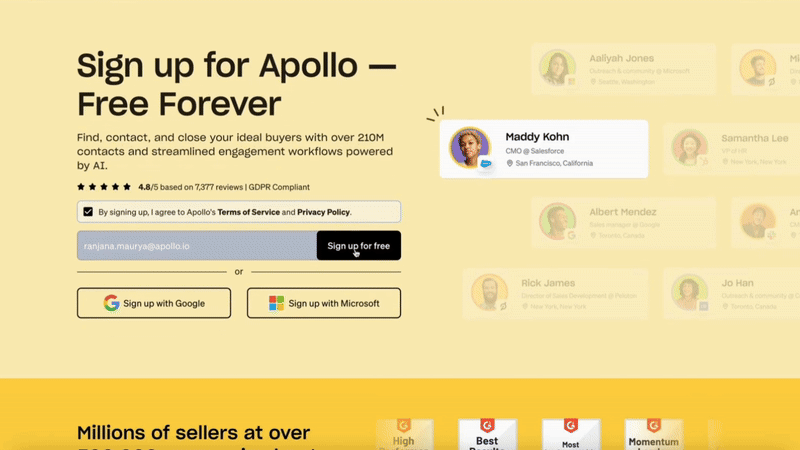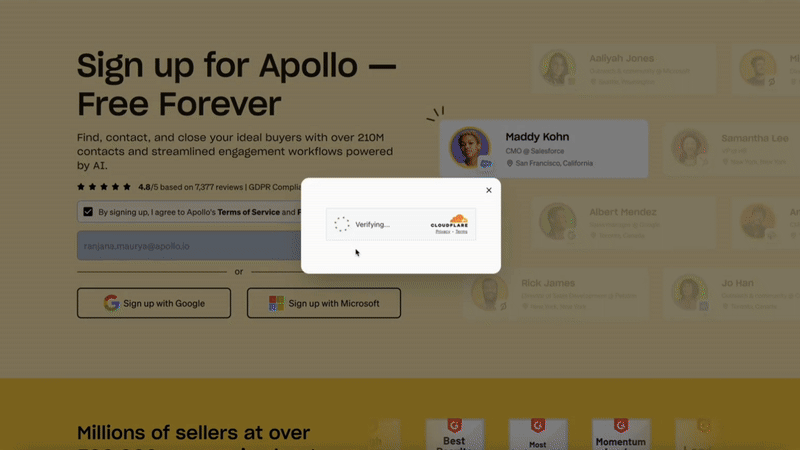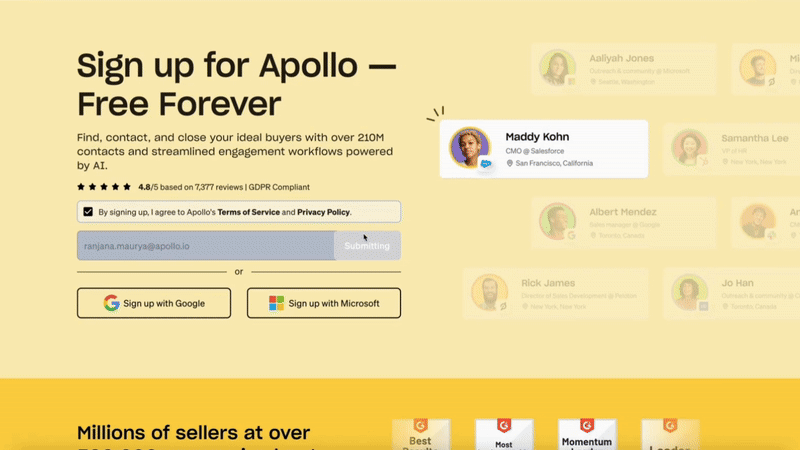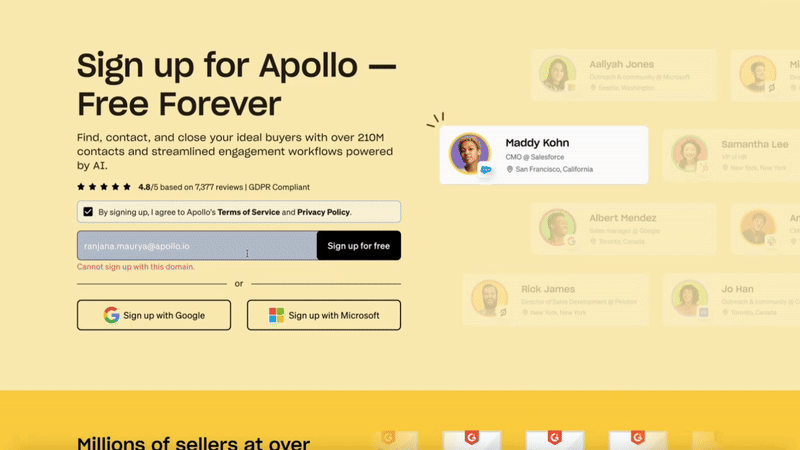
The Turnstile widget appears only when necessary, seamlessly overlaying the current flow without triggering a page reload or reset. Once the challenge is completed, the intended action resumes automatically, without requiring any additional user input.
-
-
Edge-Layer Enforcement
- Cloudflare® Workers inspect backend responses and enforce challenge workflows by injecting Turnstile logic directly at the edge.
2. Data-Driven, Adaptive Triggers
We don’t rely on guesswork. Our challenge decisions are based on multiple criteria, with some high-level examples listed below:
- Cloudflare® WAF & Bot Scores WAF applies security rules to incoming requests, while the Bot Score (1–99) estimates how likely a request came from a bot—helping us decide when to trigger a challenge.
- Apollo-Specific Abuse Signals
- Unusual team activity — identified through custom in-app behavioral signals tailored to detect specific activity patterns
- Bot signatures
- Repeated hits to critical endpoints
This dual-layer logic leads to lower false positives, high challenge precision, and a seamless UX for trusted users. By combining Cloudflare® intelligence with Apollo-specific signals, we've created a system that intelligently differentiates between legitimate users and potential threats.
3. Multi-Surface, Extensible Rollout
- Unified Challenge Handling
- Marketing site, app, and Chrome extension follow a consistent challenge workflow.
- Endpoint-Specific Widgets
- Each integration logs its metrics, allowing granular observability.
- Configurable Expansion
- Adding new endpoints only requires configuration changes, not code rewrites.
🔬 Tech Deep Dive: How It Works
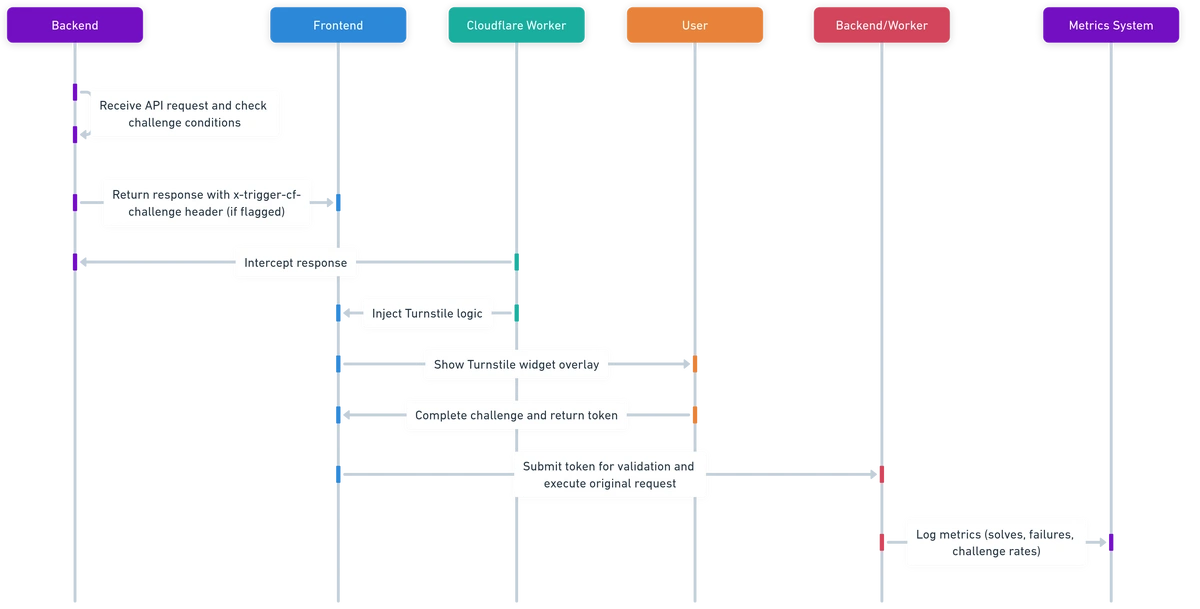
Here's a behind-the-scenes look at our security architecture that balances robust protection with seamless user experience, leveraging both Cloudflare® capabilities and our custom implementation. This project's success stemmed from strong collaboration with Platform and Security Engineering teams. Special thanks to the backend platform team for driving the proof-of-concept implementation, Cloudflare® Worker logic, and dashboarding & observability tooling that made this possible. Here's a behind-the-scenes look at our security architecture that balances protection with seamless user experience:
- Backend receives an API request and checks for challenge conditions.
- If flagged, it returns a challenge flag attribute as part of the response header.
- Cloudflare® Worker intercepts the response and injects Turnstile logic.
- Frontend shows the Turnstile widget overlay.
- User completes the challenge; one-time token is returned.
- Backend/Worker validates the token and executes the original request.
- Metrics are logged: solves, failures, challenge rates by team/user.
📈 Impact by the numbers
We closely monitor several key metrics, including challenge success and failure rates for each endpoint, login/signup trends before and after deployment, attribution of malicious traffic sources (organized by domain, team, and IP cluster), and the impact on conversion rates for our legitimate paid users.
🚫 On average, 98%+ Malicious API Calls Blocked
- One of our prospecting endpoints alone saw malicious API calls rejected by up to 99% for free teams.
🔐 2.6M Credential Stuffing Attempts Blocked
- All blocked with 0% solve rate—bots couldn’t pass the Turnstile.
✅ Legitimate Login Success Improved
- Success rate during attack periods rose by 12%.
😌 Minimal Real User Friction
- Only hundreds of challenges triggered (vs millions of hits).
- Free teams resolved challenges at ~2.2% compared to 83.3% for paid teams — highlighting a clear gap in successful completions.
🔧 Reduced Ops Burden
- No more hot patches or emergency blocks.
- Abuse vectors are now blocked by config, not code pushes.
🌐 Platform-Wide Coverage
- App, marketing site, and browser extension now share a unified protection model.
🏁 Lessons Learned & Road Ahead
Throughout this project, we've discovered that precision beats brute force - targeted challenges are far more effective than generic ones. We've also learned that visibility matters, as robust metrics allow us to tune and evolve our security policies more quickly. Finally, we recognize that security is ongoing - our protection strategies must continually expand as our platform's surface area grows.
Huge shoutout to Jon Ferrari, our Senior Manager of Fraud and Abuse, for passionately leading the charge on this defense. His intuition, quick action, and deep expertise played a critical role in stopping this attack in its tracks.
Equally big thanks to Neil Ongkingco from our Backend Platform Engineering team for crafting a resilient and efficient backend layer that held strong under pressure—your work made this defense possible.
Want to Connect? We are hiring!
Apollo is hiring! Join us to tackle challenges like scaling defenses against millions of malicious requests, balancing security with seamless user experience, and building adaptive systems for real-world threats. We would love for smart engineers like you to join our "fully remote, globally distributed" team. Click here to apply now!